Yesterday afternoon, Ars Technica published an article about a “white hat” hacking incident. Certain Asus routers have a vulnerability in the AiCloud service (Asus’ proprietary web service, which enables FTP and Samba/ file sharing, among other things) whereby an unauthenticated user from the Internet could gain access to hard drives connected to the USB port on the router, either to read data off the drive, or write new data to the drive. This vulnerability was in fact reported last June, but not fixed by the vendor until last week.
The Ars Technica article describes an unsuspecting user finding an unexpected text file on his hard drive, a text file describing the flaw and calling Asus out for not fixing it 8 months after responsible disclosure.
Asus did release a patch on February 13 that purportedly fixes this flaw, but alas another bug will undoubtedly prevent many from knowing about it. Asus routers have an option in the administrative interface to check for firmware updates, but that option itself is flawed. The below screen shot is taken from an Asus RT-AC66R router on February 18. It clearly shows Firmware version 3.0.0.4.374.2050 (released 2014-01-14 per the Asus support page), and shows that this is the current firmware for this model of router. But the very same support page shows a newer version released 5 days ago.
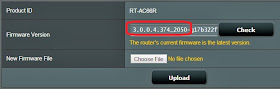 |
| Asus RT-AC66R Showing outdated firmware as current |
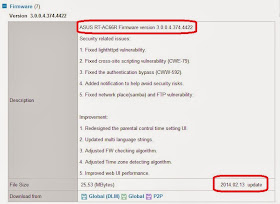 |
| Asus RT-AC66R actual latest firmware |
Clearly it is not enough to rely on this vendor’s built-in firmware update mechanism, but I suspect many that own these routers will do just that, giving them the false expectation that they are up to date. Many vendors have had years of “hard knocks” experience through which they have come up with relatively robust processed for delivering software updates to consumers. Microsoft, Apple, Adobe, Oracle (owner of Java) fall into this category. Unfortunately not every vendor has learned that lesson yet.
This is not the only cloud-based router vulnerability to turn up this month. Higher-end Linksys home routers started using a feature they call “Smart Wi-Fi” around March 2012, a feature that is designed to reduce home user vulnerabilities by removing the configuration from the user. Configuration of your home router is managed by the cloud. I in fact returned a Linksys router once I realized I had no local control over its configuration – and that I had to connect it to the Internet and create an account with Linksys before I could enable any security settings. As I wrote at the time, that is a completely backwards approach, and one that is bound to lead to new ways of home network compromise.
Fast forward to 2014, and my prediction has unfortunately come true. On February 13 (ironic date, don’t you think?) the SANS Internet Storm Center reported a new worm spreading among Smart Wi-Fi-enabled models of Linksys routers. The worm uses precisely the feature I worried about – it uses the CGI script built in to the router, which the cloud-based administrative system uses to manage the router (and which oddly does not verify the random admin “credentials” given it by the worm). The worm is known to search for other vulnerable routers to infect, but has not (yet) been shown to do more than simply spread. That said, the vulnerability is now known and could just as easily be exploited with more damaging consequences (such as modifying settings so as to intercept banking traffic).
Bottom line? As much as vendors would like to deny it, setting up a secure home network is not plug and play. It behooves you to understand at least the basics, or to consult with someone that does. Ensure your router and connected devices (computers, tablets, Internet TVs, game consoles, etc) are all updated with the latest firmware and patches available from the vendor - and don't always rely on the auto-update or auto-check feature. Use a non-default and hard-to-guess password for anything that matters to you. Enable WPA2 encryption on your wireless networks. And know what "normal" looks like for your devices so you can tell if something is out of the ordinary.

