In mid February, I wrote that a substantial portion of ASUS wireless routers would fail to update their firmware. In fact, the "check for update" function would inform the administrator that the router was fully up-to-date, even though it was not. The server tables that identify the correct latest firmware revision for each model of router had not been updated in about 4 months, though there had been two releases in the interim. This was a significant problem because it came right on the heels of an exploit for a bug in which hard drives connected to the router could be accessed from the public Internet, with no login credentials required.
This report is one in a series I have written on ASUS wireless router features and vulnerabilities. Others of interest:
|
ASUS was very quick to fix this (and rightly so - the fix was very simple, an update to the text file that the router parses to determine if it needs an update). In analyzing that issue though, I saw some things that looked like potential avenues of exploit. Several of those have proven true.
The Web GUI for the ASUS RT- series of routers exposes the administrator username and password in clear text. This is true for the RT-AC68U, RT-AC68U, RT-AC66R, RT-AC66U, RT-AC56R, RT-AC56U, RT-N66R, RT-N66U, RT-N56R, RT-N56U models. I have not tested but suspect the same is true of RT-N53, RT-N14U, RT-N16, and RT-N16R since they use the same firmware base but a different sub-version. I have submitted this as CVE-2014-2719.
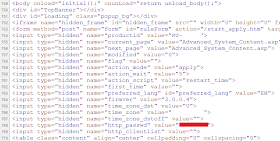
Having a logged in session, the page <router-ip>/Advanced_System_Content.asp contains the current administrator username and password, in clear text, as a hidden variable:
If the administrator is logged in, an attacker can browse to <router_address>/Advanced_System_Content.asp and obtain the username and password. Researcher Bogdan Calin demonstrated a way to access the router via embedded images in an email message 18 months ago; that combined with this would gain an attacker easy administrative access.
Compounding the problem, the admin login does not have a session timeout. Thus, if the administrator logged in (such as when first configuring the router, or subsequently installing an update) and does not intentionally logout, the session remains live and can be exploited as described above, even if the administrator no longer has a window open on the router.
This is only effective if the attacker can compromise a computer with a live session to the router. However, if the attacker can compromise any host on the target network, and attempt to login to the router, the router informs them of the IP address from which someone is currently logged in.
Firmware
Update April 17 6:00am It looks like ASUS is slowly rolling this firmware out for the different models. As of this morning, firmware 3.0.0.4.374.5517 is only available for the following models:
RT-AC66U
RT-AC66R
RT-N66U
RT-N66R
Update April 24 9:00am I received a message from Asus this morning stating that firmware 3.0.0.4.374.5656 will post to support sites today for all affected models and addresses this bug as well as some stability enhancements. Release notes follow:
RT-AC68U/ AC68R/ AC68W
Security related issues:
1. Fixed password disclosure in source code when administrator logged in.
2. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
Others:
1.Fixed wake on Lan magic packet sending issue.
2.Fixed false alarm for samba and ftp permission.
3.Fixed IPv6 related issues.
4.Samba/ media server/ iTunes server name can be changed.
Special thanks for David Longenecker and Joaquim Brasil de Oliveira’s research
Others:
1.Fixed wake on Lan magic packet sending issue.
2.Fixed false alarm for samba and ftp permission.
3.Fixed IPv6 related issues.
4.Samba/ media server/ iTunes server name can be changed.
Special thanks for David Longenecker and Joaquim Brasil de Oliveira’s research
CVE-2014-2719 https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Cross Site Scripting: https://web.nvd.
Remote Command Execution: https://web.nvd.
RT-AC56U/ AC56R
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
8. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
Others:
1. Added universal beamforming to enhance the wireless speed for non 802.11ac devices
2. Fixed IPTV related issues.
3. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
4. Fixed the Cloud sync problem
5. Fixed Parental control check box UI issues.
6. Modified the FTP/ Samba permission setting UI
7. Modified media server setting UI
8.Samba/ media server/ iTunes server name can be changed.
9. Dual wan fail over now support fail back
10. Fixed wake on Lan magic packet sending issue.
11. Fixed false alarm for samba and ftp permission.
12. Fixed IPv6 related issues.
13. Supported HFS+
14. Supported Time machine
Special thanks for David Longenecker and Joaquim Brasil de Oliveira’s research
CVE-2014-2719 https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Cross Site Scripting: https://web.nvd.
Remote Command Execution: https://web.nvd.
RT-N56U
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
Others:
1. Fixed IPTV related issues.
2. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
3. Fixed Parental control check box UI issues.
4. Modified the FTP/ Samba permission setting UI
5. Modified media server setting UI
6. Samba/ media server/ iTunes server name can be changed.
7. Fixed wake on Lan magic packet sending issue.
8. Fixed false alarm for samba and ftp permission.
9. Fixed IPv6 related issues.
1. Fixed IPTV related issues.
2. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
3. Fixed Parental control check box UI issues.
4. Modified the FTP/ Samba permission setting UI
5. Modified media server setting UI
6. Samba/ media server/ iTunes server name can be changed.
7. Fixed wake on Lan magic packet sending issue.
8. Fixed false alarm for samba and ftp permission.
9. Fixed IPv6 related issues.
Special thanks for David Longenecker and Joaquim Brasil de Oliveira’s research
CVE-2014-2719 https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Cross Site Scripting: https://web.nvd.
Remote Command Execution: https://web.nvd.
RT-AC66U/ AC66R
Security related issues:
1. Fixed remote command execution vulnerability
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed cross site scripting vulnerability
3. Fixed parameters buffer overflow vulnerability
4. Fixed XSS(Cross Site Scripting) vulnerability
5. Fixed CSRF(Cross Site Request Forgery) vulnerability
6. Added auto logout function. The timeout time can be configured in - Administration--> System
7. Included patches related to network map. Thanks for Merlin's contribution.
8. Fixed password disclosure in source code when administrator logged in.
9. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
3. Fixed parameters buffer overflow vulnerability
4. Fixed XSS(Cross Site Scripting) vulnerability
5. Fixed CSRF(Cross Site Request Forgery) vulnerability
6. Added auto logout function. The timeout time can be configured in - Administration--> System
7. Included patches related to network map. Thanks for Merlin's contribution.
8. Fixed password disclosure in source code when administrator logged in.
9. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
Others:
1. Fixed IPTV related issues.
2. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
3. Fixed the Cloud sync problem
4. Fixed Parental control check box UI issues.
5. Modified the FTP/ Samba permission setting UI
6. Modified media server setting UI
7.Samba/ media server/ iTunes server name can be changed.
8. Dual wan fail over now support fail back
9. Fixed wake on Lan magic packet sending issue.
10. Fixed false alarm for samba and ftp permission.
11. Fixed IPv6 related issues.
Special thanks for David Longenecker and Palula’s research
CVE-2014-2719https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Remote command execution http://seclists.org/fulldisclosure/2014/Apr/58
Reflected XSS: http://seclists.org/fulldisclosure/2014/Apr/59
RT-N66U/ N66R/ N66W
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed cross site scripting vulnerability
3. Fixed parameters buffer overflow vulnerability
4. Fixed XSS(Cross Site Scripting) vulnerability
5. Fixed CSRF(Cross Site Request Forgery) vulnerability
6. Added auto logout function. The timeout time can be configured in - Administration--> System
7. Included patches related to network map. Thanks for Merlin's contribution.
8. Fixed password disclosure in source code when administrator logged in.
9. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
Others:
1. Fixed IPTV related issues.
2. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
3. Fixed the Cloud sync problem
4. Fixed Parental control check box UI issues.
5. Modified the FTP/ Samba permission setting UI
6. Modified media server setting UI
7.Samba/ media server/ iTunes server name can be changed.
8. Dual wan fail over now support fail back
9. Fixed wake on Lan magic packet sending issue.
10. Fixed false alarm for samba and ftp permission.
11. Fixed IPv6 related issues.
CVE-2014-2719 https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Remote command execution http://seclists.org/fulldisclosure/2014/Apr/58
Reflected XSS: http://seclists.org/fulldisclosure/2014/Apr/59
RT-N16
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed cross site scripting vulnerability
3. Fixed parameters buffer overflow vulnerability
4. Fixed XSS(Cross Site Scripting) vulnerability
5. Fixed CSRF(Cross Site Request Forgery) vulnerability
6. Added auto logout function. The timeout time can be configured in - Administration--> System
7. Included patches related to network map. Thanks for Merlin's contribution.
8. Fixed password disclosure in source code when administrator logged in.
9. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
2. Fixed cross site scripting vulnerability
3. Fixed parameters buffer overflow vulnerability
4. Fixed XSS(Cross Site Scripting) vulnerability
5. Fixed CSRF(Cross Site Request Forgery) vulnerability
6. Added auto logout function. The timeout time can be configured in - Administration--> System
7. Included patches related to network map. Thanks for Merlin's contribution.
8. Fixed password disclosure in source code when administrator logged in.
9. Changed OpenSSL Library from 1.0.0.b to 1.0.0.d. Both OpenSSL versions are not vulnerable to heartbleed bug.
Others:
1. Fixed IPTV related issues.
2. Modified the 3G/LTE dongle setting process in quick internet setup wizard.
3. Fixed the Cloud sync problem
4. Fixed Parental control check box UI issues.
5. Modified the FTP/ Samba permission setting UI
6. Modified media server setting UI
7.Samba/ media server/ iTunes server name can be changed.
8. Dual wan fail over now support fail back
9. Fixed wake on Lan magic packet sending issue.
10. Fixed false alarm for samba and ftp permission.
11. Fixed IPv6 related issues.
CVE-2014-2719 https://securityforrealpeople.com/2014/04/CVE-2014-2719-Asus-RT-Password-Disclosure.html
Remote command execution http://seclists.org/fulldisclosure/2014/Apr/58
Reflected XSS: http://seclists.org/fulldisclosure/2014/Apr/59
RT-N12HP
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
Others:
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Supported Dual wan
RT-N12 D1
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Supported Dual wan
RT-N12 D1
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
Others:
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Supported Dual wan
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Supported Dual wan
RT-N10U/ N10U B1
Security related issues:
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
1. Fixed remote command execution vulnerability
2. Fixed parameters buffer overflow vulnerability
3. Fixed XSS(Cross Site Scripting) vulnerability
4. Fixed CSRF(Cross Site Request Forgery) vulnerability
5. Added auto logout function. The timeout time can be configured in - Administration--> System
6. Included patches related to network map. Thanks for Merlin's contribution.
7. Fixed password disclosure in source code when administrator logged in.
Others:
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Modified the FTP permission setting UI
1. Fixed IPTV related issues.
2. Fixed Parental control check box UI issues.
3. Fixed wake on Lan magic packet sending issue.
4. Fixed IPv6 related issues.
5. Modified the FTP permission setting UI
6. Modified the 3G/LTE dongle setting process in quick internet setup wizard.