This started out as a story of lax security at one of the biggest providers of corporate retirement services. As I researched though, it has become a lesson about layers of security. All in all, the company described does a pretty good job, and is making even more improvements.
This started out as a story of lax security at one of the biggest providers of corporate retirement services. As I researched though, it has become a lesson about layers of security. All in all, the company described does a pretty good job, and is making even more improvements.If you have an account with Fidelity Investments (including their 401k.com and NetBenefits properties), take a minute to update your password, then read on. This time the reason is beneficial, and not breach-related: Fidelity recently updated the password rules to allow a significantly stronger password. tl;dr: jump to the end for a few quick tips.
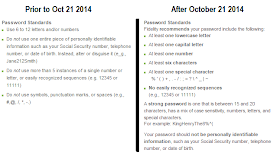
According to their corporate fact sheet Fidelity is the largest provider of 401(k) savings plans, serving over 20,000 employers and 20 million individuals, with over $4.5 billion in assets (this number includes non-retirement accounts). This includes a number of Fortune 500 companies. Prior to October 2014, the company websites would not allow one to create a very strong password. Passwords were limited to letters and numbers. With the recent changes, the websites now support upper and lower case alpha characters, numbers, and a partial list of special characters ( % ' ( ) + , . - / : ; = ? \ ^ _ | ~ ).
Skip this paragraph if math intimidates you
This increases the number of available characters from 62 (A..Z, a..z, and 0..9) to 80 (the original 62, plus 18 special characters). Mathematically, you'll get more brute force benefit out of making your password one character longer than you do out of taking advantage of a larger character set. Suppose you have a 12 character password using the original 62-character set. There are 62^12 possible passwords (12 spaces, each of which can be any one of 62 characters). Making the password one space longer creates a solution space of 62^13 permutations - significantly larger than the 80^12 possibilities that come from the larger set of allowable characters.
Let's look at a simpler scenario: assume only the digits 0-4 are allowed, and you have a 2-digit password. There are 25 possible passwords (2 spaces, each of which can be any of 5 characters - 5^2 is 25). Doubling the allowed characters to 10 (0 through 9) makes 10^2 or 100 possible passwords, while making the password only one character longer makes 5^3 or 125 possible passwords. The math gets exponentially larger as the password size grows. Against a brute force attack (i.e. an attacker that tries each possible password trying to work out the correct password through brute force), a longer password is far stronger than a password that uses more characters.
No more math!
 Math aside, a long password matters more than the variety of letters, numbers, and symbols used in that password. We tend to make things easy by choosing silly passwords - "password123" for example, or maybe a child's name and birthday - "William99" for example. A password manager can help by generating truly random passwords - and then will remember the password so you don't have to. Truth be told, there is no such thing as an impossible-to-crack password. Given enough time and computing power, it will always be possible to try every single possible combination and eventually discover the right one. Choosing a strong password simply makes it more difficult. Instead of being able to crack a password given a few minutes with a lowly laptop, it might take days with a massive computer farm - too much effort unless you are an especially valuable target. Or the attacker turns to a keyboard logger or phishing web page to capture the password as you log in, making the relative strength of the password irrelevant. Practically speaking though, adding special characters reduces the temptation to use common dictionary words that an attacker might guess, taking away the easiest attack option. Of course you don't use dictionary words, right? The point is, passwords can be compromised, but choosing a strong password at least takes away the easiest way. This is also why I and most security professionals recommend two-factor authentication (which relies on something you have in addition to a password - for instance, a cell phone or a code-generator device) as a strong way to limit the risk of a stolen password.
Math aside, a long password matters more than the variety of letters, numbers, and symbols used in that password. We tend to make things easy by choosing silly passwords - "password123" for example, or maybe a child's name and birthday - "William99" for example. A password manager can help by generating truly random passwords - and then will remember the password so you don't have to. Truth be told, there is no such thing as an impossible-to-crack password. Given enough time and computing power, it will always be possible to try every single possible combination and eventually discover the right one. Choosing a strong password simply makes it more difficult. Instead of being able to crack a password given a few minutes with a lowly laptop, it might take days with a massive computer farm - too much effort unless you are an especially valuable target. Or the attacker turns to a keyboard logger or phishing web page to capture the password as you log in, making the relative strength of the password irrelevant. Practically speaking though, adding special characters reduces the temptation to use common dictionary words that an attacker might guess, taking away the easiest attack option. Of course you don't use dictionary words, right? The point is, passwords can be compromised, but choosing a strong password at least takes away the easiest way. This is also why I and most security professionals recommend two-factor authentication (which relies on something you have in addition to a password - for instance, a cell phone or a code-generator device) as a strong way to limit the risk of a stolen password.
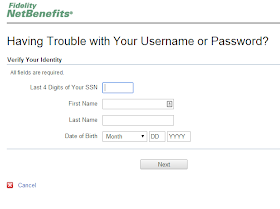
But a password is not the only way into an account. What happens when you forget your password? Every account provider has some way of resetting a forgotten password, and often the password reset mechanism is far easier to compromise than the password itself. That is true of 401k.com too. To reset a 401k.com password, a person must know first and last name, birthdate, the last 4 digits of a SSN, and the answer to a “security question.” Name and birthdate are not exactly hard to come up with. Many people guard their full SSN, but may not closely guard the last 4 digits – in fact many utility and telephone companies use the last 4 digits to validate an account holder. That essentially means that an attacker only has to uncover the answer to the security question. Until recently the answer to that security question could only be a 4-digit number – the last 4 digits of your best friend's phone number, or the last 4 digits of your "favorite credit card." Really? With a 4-digit number you can "verify your identity" and reset the password granting access to what could amount to a person's life savings?

According to a recent report, the average 401(k) at the end of 2013 had a balance of just shy of $90,000; for those age 55 and up (presumably those nearing retirement), the average balance was $165,000. Putting aside for a moment the fact that $165,000 won't last very long when funding a post-work life that could surpass three decades, that's a significant amount of savings to have protected by the last 4 digits of one's best friend's phone number.
That's the bad news.
However, that only tells part of the story. Fidelity has been making gradual improvements this year, and has more improvements in store. In addition there are some behind-the-scenes factors that limit the risk of financial fraud when it comes to retirement accounts.
In recent months Fidelity changed the password rules, as described above. The company also changed the "Security Question" options to now allow longer, text responses. Of course many of the options are things someone might be able to discover - where did you go to school, what street did you grow up on, what is your favorite restaurant. There's an easy way to improve upon this though: lie! What was your first car? An orange. What town were you born in? Tatooine. The same password manager that can remember your passwords can also remember the password reset questions, so you can lie with impunity.
Any significant update - changing passwords, changing email or mailing addresses, changing contribution amounts, initiating a withdrawal - results in either an email or physical letter (sent to the original address in the event of a change). In addition, if Fidelity services the retirement account for your current employer, personal information changes (mailing address, for instance) must come from the employer - there is no way for a fraudster to change your mailing address without first compromising your employer's records (and even then, you would receive a letter at your old address).
The lesson is this: personal and financial security are best served by a layered approach, so that if one layer fails, there is another layer to back it up. Two-factor authentication means a stolen password is no use without also stealing (and breaking into to) the phone or code generator. Regulations between employer and retirement service provider mean certain actions would require compromising the employer in addition to access the specific account. Confirmation letters (sent to the original address in the event of a change) provide an alert to any nefarious activity.
Five quick tips
- Change your password at Fidelity
- Password (or pass-phrase) length matters more than complexity. A sentence makes a great password.
- Where possible, use two-factor authentication, which combines a password with something you possess, such as your phone.
- Lie on your password reset questions.
- Let a password manager remember your passwords for you.