Updated 29 November with additional context after I analyzed the malicious link. TL;DR: Tom Hanks is not dead, and the fake news link on Facebook leads to a malicious website. As an aside, Tom Hanks is not the first celebrity to be used in fake news scams, and I am sure he won't be the last. Other recent malvertisements have claimed the demise of Harrison Ford, Sylvester Stallone, Beyonce, and even Facebook's own CEO Mark Zuckerberg.
No, Tom Hanks is not dead. However, a malicious advertisement circulating on Facebook over Thanksgiving weekend uses that headline as bait; readers that click the "news story" to find out more instead get more than they bargained for.
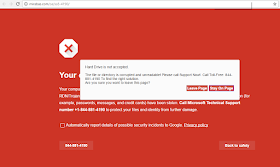
Instead of a news article, the advertisement leads to a web page that blares an incessant alarm sound and displays the following warning message. As a clever twist, the malicious content itself imitates Google's own malicious website warning.
Victims that call the phone number on the screen will no doubt be instructed to pay a "Microsoft Technical Support" fee to have the malware removed - a twist on the classic technical support scam.
The red screen above will look familiar to many readers: Google's Chrome browser, along with Mozilla Firefox and Apple Safari, are part of the Google Safe Browsing project. These browsers display a warning such as the one below before opening a website Google has determined to be malicious or deceptive.
However, the real Google Safe Browsing warning does not include wailing sirens and incessant popup messages. Nor does it claim you have already been infected and direct you to call a technical support number for assistance. The purpose of Safe Browsing is to warn you before you open a dangerous web site:
As the US Federal Trade Commission describes, technical support scams are a common method crooks use to separate you from your money. The classic approach is, you run a "free antivirus check" website, which informs you that you are infected by all sorts of nastiness. A more recent variation is, you get a phone call from someone pretending to be "Microsoft Technical Support," claiming again that your PC is infected. In both cases, the crooks' goal is to trick you into giving them remote access or paying for "cleaning" that you don’t need.
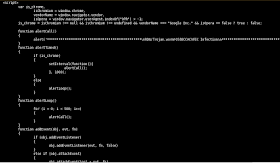
In this case, the scam appears to be purely social engineering, and not a technical exploit. The page does not actually download any malware to the PC. Instead, it uses a JavaScript loop to keep the warning message on screen if a reader tries to cancel the warning, and another JavaScript routine to keep the reader from closing the browser window.
The following message is displayed atop the red warning screen, and refreshes every second if you try to close it. This technique is particularly annoying because it interrupts any other browser windows to make you acknowledge the alert... which of course returns almost immediately once you acknowledge it.
What can you do?
- If you have encountered this, or any other website displaying a popup alert that your PC is infected, use the Escape key to close the popup warning - and immediately press CTRL-F4 to close the browser tab before the popup returns.
- This scam relies on JavaScript, a feature of modern browsers that enables interactive websites, but that also can be abused to enable terrible browsing experiences. Disabling JavaScript will thwart this scam, though may break other websites. Here is how to disable JavaScript.
- Replace the domain name service provided by your ISP with a malware-blocking DNS such as OpenDNS - it's easy and extremely effective. DNS is how your computer translates "website.com" into a computer-understandable address. If you try to go to a known-malicious site, OpenDNS simply changes the address and sends you to a page saying "you don't really want to go there."
Full disclosure: this only works after a site has been deemed malicious; if you are among the first to visit a new malicious site, OpenDNS doesn't yet know it is malicious and so won't stop you. Still, it is a very strong addition to your home or business network security.