Time for another phishing lesson. Today's lesson involves a fake email pretending to be from Apple, which tries to steal not only your Apple ID login information, but everything else necessary to fully impersonate your identity: a credit card number with expiration and security code; mailing address; date of birth; social security number; and oh yes, your favorite security question.
Unlike many phishing attempts, this scam is quite professionally done. Other than the obscene amount of personal information it collects to "verify" your account, there is not much to indicate it is fraudulent once you have clicked the link.
#firstcon15
It's no longer about new malware techniques, it's about social engineering users into bypassing their own banks protections!
— ChrisJohnRiley ✪ (@ChrisJohnRiley) June 15, 2015
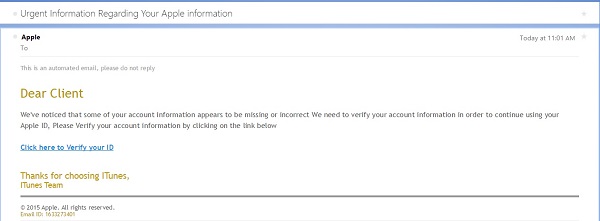
Today I received an email claiming to be from Apple, regarding a problem with my Apple ID, and inviting me to verify my account information. Coincidentally I had mis-typed my password in iTunes yesterday and got a warning message that I would need to re-verify my account, so the timing might have been fortuitous for a phisher if I were less observant.
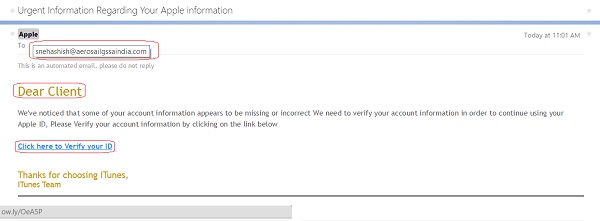
There are a couple of clues in the email that something is not right - but you have to look for them. First, while the email title says "Apple," if you hover over the address, you can see the actual address is someone at aerosailgssaindia (and my bet is that is not the actual attacker's address, but rather a stolen email account being used to send spam).
Second, the greeting says "Dear Client" rather than greeting me by name. Apple says they will use your real name in the greeting for any legitimate message.
Third, this email was sent to an address that I used in the past, but no longer use. I have updated most services with my new email - but I could not be 100% certain I had updated my Apple ID.
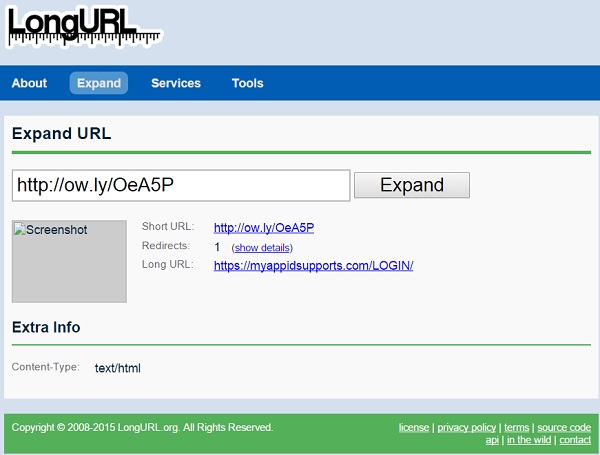
Fourth, hovering over the link reveals a URL using URL shortener service ow.ly. While shortened URLs are common in social media and other places where a long URL is unwieldy, there is no reason for a link in an email message to not use the correct URL - which one would expect to be something at apple.com.
I am not one to click random links in email, so I used the "URL expander" service longurl.com to figure out the actual destination. In this case, the link expands to myappidsupports [dot] com/LOGIN/. But look - it's secure! It begins with https:// so it's secure, right? Well, sure - you can securely talk to a crook, knowing that no other crook can eavesdrop on your conversation!
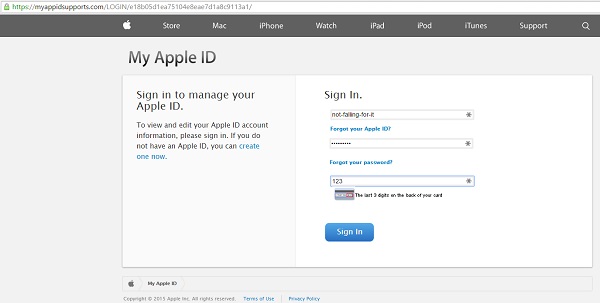
Having convinced myself that this was not a legitimate message from Apple, I pulled up the link on my test system (I don't recommend following suspicious links from a system that matters to you). Lo and behold, it is a convincing imitation of a support site for Apple ID problems, asking me to log in. But what's this - it also wants the CVV (security code) from my credit card? Well, why not!
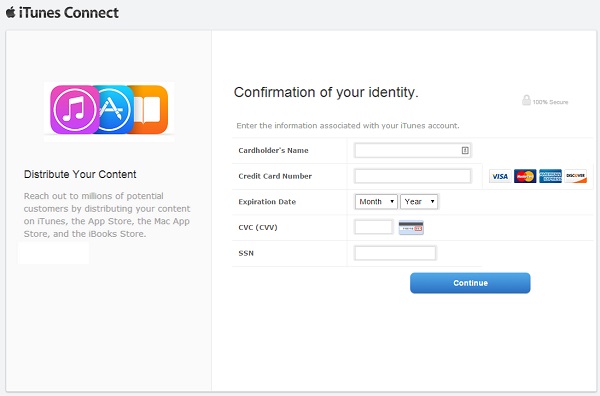
Oh, but that's not all. After "logging in" (with a bogus username and password), the phisher then would like me to verify my credit card information. I do not keep a credit card on my Apple account. The legitimate Apple website does not require a credit card (unless of course I try to buy something). This site however will not let me proceed without entering something.
Even better, this form requires a SSN. Now think about it, why does a music and app store need my social security number? There is no legitimate reason.
Of course, why stop at stealing a credit card number and SSN? This scam goes for broke, with one last screen designed to capture anything else I am willing to divulge: home address, phone number, date of birth, and even a "Question of Security." Needless to say, by this point I have some "questions of security."
To complete the illusion, the final step upon clicking "Finish" is to load the legitimate iTunes Connect website, which is in fact a legitimate Apple website. If I did not know better, I might think I had safely verified the information on my account, and now needed to log back in to my Apple account.
The lesson here is that phishing is a serious problem. Scams vary, but in many cases criminals go to great lengths to prepare a very convincing scam. I documented a case last year of a phish targeting USAA members: the criminals had completely duplicated the legitimate USAA website, and even loaded the style sheets and images from the actual site so as to be a perfect clone. Since the scams are not always obvious, it falls to us to protect ourselves. A few suggestions:
- Look at email with a bit of caution. Was the message sent to the email address you gave to a service provider? Does it address you by name? A legitimate message from a business will generally say "Hi David" or "Dear Mr. Longenecker," whereas a phish will often say say "Hello Client" or "Dear HappyClams_83," assuming your name to be the same as your email address.
- Hover over any links with your mouse, and look at the status bar at the bottom of the browser. While there are ways to disguise the URL - and an attacker specifically targeting you or your business will go to the effort of making the fake link look real - most often a generic phish will use an obviously bogus URL.
- Only log in or provide personal information if you typed the link yourself or used a bookmark you saved yourself. Not every link that comes by email is fraudulent, but the safest approach is to simply not click links in email.
- Use a DNS (domain name service, or "phone book") such as OpenDNS that will block known phishing and malicious links. This can protect you from accidentally browsing to a malicious web site.
- Protect your personal information. Information that you share on Facebook can be used to craft a phishing scam specifically for you, using a business you use, or pretending to be a friend or family member.
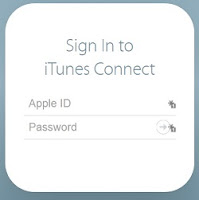
- One final tip: I use LastPass to store my passwords for online accounts. It has an additional feature that is useful for preventing me from entering passwords into fake sites: since LastPass knows which website goes with which passwords, it puts a marker beside the login fields for sites it knows (note the "1" beside the ID and password fields in the image on the left). Conversely, if a site asks me to log in and LastPass does not show the marker (as in the image on the right), it very likely is a site I have never logged into before.
Update 27 June: Evidently one scam attempt is not enough, so today I received a variation on the same phish; the subject and the URL linked to the "Click here to Verify your ID" instruction was different, but the rest of the scam was the same.
Email subject 1: Urgent Information Regarding Your Apple information
Phish URL 1: myappidsupports [dot] com/LOGIN/
Email subject 2: Urgent Account Review <date and time>
Phish URL 2: http://login.kaymushop [dot] com/Apple/