Fellow Austin security pro Michael Gough first introduced me to the idea of malware hiding in the Windows registry a couple of years ago. It's sneaky but it makes sense: most antivirus products depend on a malicious file existing on the hard drive. They scan the disk periodically for malicious programs, and will scan files written to or read from the disk when that read or write occurs.
If malware files never touch the disk, then when will antivirus scan them?
Exactly.
Last week, another researcher wrote about this technique in Stealth Techniques: Hiding Files in the Registry. If you are unfamiliar with how a program might be stored in the registry, Alex Abramov's blog post is an excellent and in-depth explanation. Essentially, a malware program is converted into a blob of binary or text data - much the same way a file is handled when it is attached to an email - and then stored as a registry value.
His post brought this technique back to the front of my mind, and got me thinking of how to detect malware using the registry as a hiding place.
The Windows registry is something of a hodgepodge of information about system hardware, installed programs, settings and user preferences, and information about users of the computer. When you tell Windows Explorer that you want to see extra large icons, or conversely that you want to show file details, Windows quietly saves that preference in the registry.
Essentially, it is a database that exists in a handful of system files - and a location that few people have reason to look unless they have a system administration role.
Of note, most of the contents of a Windows registry are relatively short pieces of information, for instance:
ProductName: Windows 8.1 Enterprise
update_url: http://clients2.google.com/service/update2/crx
InstallDir: C:\Program Files\iTunes\
In other words, a massive blob of data in the registry should stand out as unusual. How do you scan through the entire registry though looking for "unusual?" It's a bit like asking someone to look through an entire encyclopedia and point out any unusual stories. Sure it could be done, but it wouldn't be fun.
Software company NirSoft makes a utility called RegScanner that can do this, but it's a GUI program and gives its results in a GUI as well. That's handy for a single system, but it's not very helpful when looking at a large number of systems. For that, most administrators prefer something that can be used from a command line or shell (and thus can be called from a script to run on many systems at once).
Alas, a command-line way to search specifically for large data items in the registry didn't exist.
Until now.
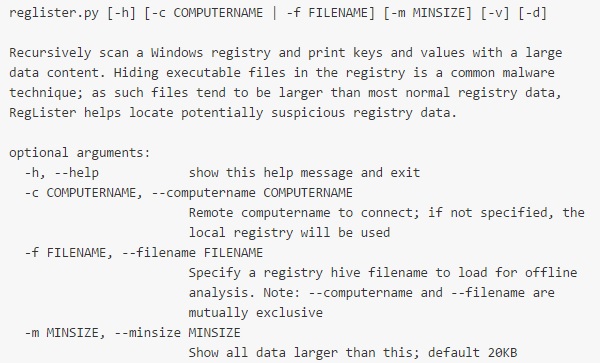
RegLister is a command-line program, written in Python, that will scan the entire Windows registry and show any large data entries.
For analyzing remote computers, RegLister accepts a "--computername" parameter. A few caveats: the remote PC must have the Remote Registry service enabled and running, and must either have its Windows Firewall disabled or set to allow incoming remote registry connections. RegLister does not currently authenticate to the remote registry, thus you must map a drive or a null session with an account with admin rights on the remote PC first.
By default, RegLister will show any entries containing more than 20 kilobytes of data. There are a small handful of legitimate Windows entries that are larger than this - but it's a very small list. The "--minsize" argument will adjust the threshold larger or smaller as desired.
In addition, RegLister has a built-in "whitelist" of legitimate Windows entries that are commonly larger than this. The utility will ignore registry entries on the whitelist, even if they are large. The built-in whitelist contains a few common entries, but can easily be extended by modifying the program code:
If you find it handy, send a tweet my way (@dnlongen) and let me know how you used it!
Update: Based on input from several readers, I've updated RegLister with a very useful feature: it now supports a "--filename" parameter to parse an offline registry file. Offline analysis is handy if you have a file collected from a suspected compromised system but do not have immediate access to the system itself. Offline analysis also cannot be tricked by a rootkit on the compromised host.
An additional benefit is that offline analysis does not depend on the Windows APIs, and thus can be run on Linux systems, which are preferred by many forensic analysts.
Software company NirSoft makes a utility called RegScanner that can do this, but it's a GUI program and gives its results in a GUI as well. That's handy for a single system, but it's not very helpful when looking at a large number of systems. For that, most administrators prefer something that can be used from a command line or shell (and thus can be called from a script to run on many systems at once).
Alas, a command-line way to search specifically for large data items in the registry didn't exist.
Until now.
RegLister is a command-line program, written in Python, that will scan the entire Windows registry and show any large data entries.
For analyzing remote computers, RegLister accepts a "--computername" parameter. A few caveats: the remote PC must have the Remote Registry service enabled and running, and must either have its Windows Firewall disabled or set to allow incoming remote registry connections. RegLister does not currently authenticate to the remote registry, thus you must map a drive or a null session with an account with admin rights on the remote PC first.
By default, RegLister will show any entries containing more than 20 kilobytes of data. There are a small handful of legitimate Windows entries that are larger than this - but it's a very small list. The "--minsize" argument will adjust the threshold larger or smaller as desired.
In addition, RegLister has a built-in "whitelist" of legitimate Windows entries that are commonly larger than this. The utility will ignore registry entries on the whitelist, even if they are large. The built-in whitelist contains a few common entries, but can easily be extended by modifying the program code:
whitelist = [
"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\PushNotifications\AppDB",
"HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify\IconStreams",
"HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify\PastIconsStream",
"HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify\IconStreams",
"HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify\PastIconsStream"
]If you find it handy, send a tweet my way (@dnlongen) and let me know how you used it!
Update: Based on input from several readers, I've updated RegLister with a very useful feature: it now supports a "--filename" parameter to parse an offline registry file. Offline analysis is handy if you have a file collected from a suspected compromised system but do not have immediate access to the system itself. Offline analysis also cannot be tricked by a rootkit on the compromised host.
An additional benefit is that offline analysis does not depend on the Windows APIs, and thus can be run on Linux systems, which are preferred by many forensic analysts.