Unfortunately even with solid security practices a business or web site may be compromised. Mistakes happen. Previously unknown software flaws are discovered. Sophisticated new attack methods are invented. Sadly though, sophisticated hacks are not usually needed: not every website follows the best security practices. Some sites fail even the most basic of precautions. It would be a real shame to log into your favorite entertainment website only to have your password stolen and used to break into your bank account.
I have long been a passionate fan of music in a wide array of flavors (mostly at the harder end of the spectrum though). I listen to rock, metal, urban, rap, country, reggae, pop, praise & worship, etc. More often than not I listen to Christian / Gospel singers. In the early days of the Internet I published CMRH, one of the more popular music-related "e-zines" (this was before the term blog had been coined), with weekly samples and reviews of new music by established and independent artists - timed to coincide with the industry convention of releasing new music on Tuesdays. My priorities changed when I started a family, so I closed CMRH in mid 2000.
Two years later (unrelated to me or my former publication) NewReleaseTuesday.com launched with a similar format, and quickly became a site I frequented. NRT now features artist spotlights, a weekly selection of free MP3s for download, videos, interviews, a calendar of upcoming releases, a weekly streaming preview of an upcoming album, and yes, reviews. It's a great source of information on the Gospel music industry.
And it is an example of security as an afterthought.
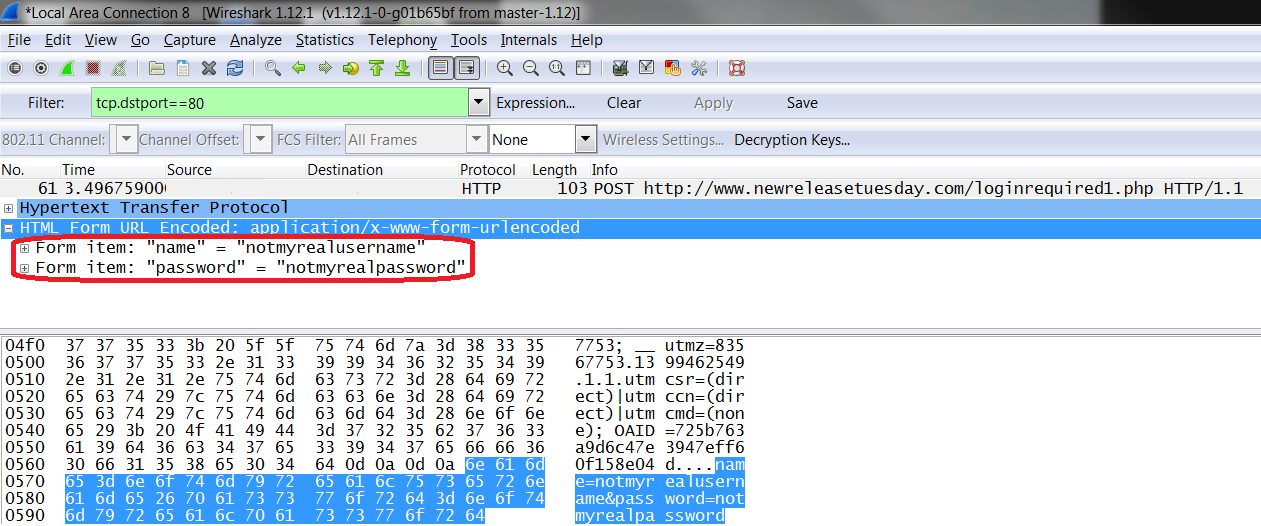
 Most of the content on NRT is freely available without registering or logging in. Some content though - notably the MP3 downloads - requires registering with an email address and password. Neither the registration page nor the login page uses HTTPS - meaning anything your browser sends to the website is sent in clear, human-readable text instead of being encrypted to avoid prying eyes. If someone can get between you and the website, they can easily read this with tools such as tcpdump or Wireshark (shown below).
Most of the content on NRT is freely available without registering or logging in. Some content though - notably the MP3 downloads - requires registering with an email address and password. Neither the registration page nor the login page uses HTTPS - meaning anything your browser sends to the website is sent in clear, human-readable text instead of being encrypted to avoid prying eyes. If someone can get between you and the website, they can easily read this with tools such as tcpdump or Wireshark (shown below).How would someone get between you and the web server without you knowing it? There are a number of ways. If you connect to a wireless hotspot that you do not own (at a coffee shop, at a hotel, at a business, at an airport ... are you certain you connected to the legitimate coffee shop hotspot and not to one set up by a hacker at the next table?), you have no way of knowing what the owner of that hotspot is doing. The administrator can easily capture network traffic, including passwords.
What's the worst that can happen if someone steals my NRT password? They might find out what kind of music I like, right?
True ... unless I also use the same password for my bank, or my email, or my Facebook. If I use the same password everywhere, then a weakness at a site I don't care about (in terms of security) can lead to a compromise at a site I care very much about.
What's true of websites is also true of apps. BBC News writes that malicious software on mobile devices takes advantage of a similar principle: mobile apps are often associated with accounts, and different apps approach security differently. A flaw in one app may expose a password, and if that password is used elsewhere, one leaky app becomes a doorway into numerous accounts.
| "[Spammers] were keen to get a foothold on a phone so they could harvest useful data that they could sell or use to make phishing emails look more plausible, or to lever open accounts for social networks or other web-based services. With 70% of people reusing passwords across many different sites and services, it was no surprise that criminals regularly got access to these accounts." |
The lesson? A little forethought with passwords goes a long way toward protecting your online identity:
- Choose a strong password - one that is not easily guessed.
- Use different passwords, at least for sites that matter. I might not necessarily be worried about using the same password for NRT and the NYTimes (for example). I would worry if I used the same password for NRT and my blog administration site. Too many passwords to remember? Then just remember one, and let a password manager remember the rest.
- Use two-factor authentication (a password plus an authenticator app or a code delivered via email or SMS) for accounts that you would be devastated to have hacked.
As an aside, I have brought this to the attention of the president at NRT. He acknowledged the condition but has no current plans to add an HTTPS server. This article is not meant to disparage that business decision, but rather to show that low security at a site that doesn't contain sensitive information can lead to a compromise at a more important site if the same password is used for both.