Before answering that question, let’s talk a little bit about Tor.
Ordinarily, when you browse to a website, certain information is available to the website, and certain information may be available to those along the path between you and the web site. Think of your connection to a website like a letter being mailed back and forth. Some pieces of information naturally have to be available – the address you are going to, as well as a return address (otherwise the website has no idea where to send the web page content). You can imagine that as the envelope, visible to anyone that can get between you and the destination.
The outside of the envelope needs to be readable so the "letter" can be sent along the correct route to the desired location. Inside the envelope are more data, data that are intended for the recipient and not necessary while the information is in transit.
The envelope - the packet header - will have the destination as a network address. Internet addresses are denoted in IP - Internet Protocol, such as 192.168.0.1. A particular address might have more than one web site though; once the request reaches the destination server, the server uses a Host header to identify the specific web site to load.
The request contains a User-Agent string, which identifies your browser. This can be used for legitimate reasons - say, optimizing the code for different browsers. It has also been used in more nefarious ways - say, offering different pricing depending on your browser (believe it or not, users of certain browsers are statistically likely to accept a higher price, and some retailers exploit that fact). Additionally, some malicious web sites recognize that certain User-Agent strings tend to suggest a researcher analyzing malware, instead of a consumer browsing the web, and so will only serve up malware to the potential victim.
The request may contain a Cookie - a piece of data stored on your computer the previous time you visited the site. This cookie may be used to customize your experience - to remember that you prefer certain settings, for example. It can also include a unique identifier that an advertising network can use to track you from site to site.
In many cases, the request may also contain information you have provided, such as a username and password, or personal information for a purchase transaction. If the website uses HTTP instead of HTTPS, as in the unfortunate example below, all of this information can be seen by anyone along the path between you and the destination. This particular website is not exactly highly sensitive - it promotes new music every week, with a few MP3s available for download each week. If someone compromises this account, the worst that happens is they may learn something about my musical tastes (I like rock. Happy?) But I make a habit of using unique passwords for every account ... many don't. If I used the same password here as I use for my email, it would be far easier for an attacker to steal this password and then try it on my more important accounts.
HTTPS encrypts the contents. Generally speaking, HTTPS means that nothing in the above screen shot can be understood by anyone other than the legitimate web site. Several events this year have shown that to not be entirely true - the Heartbleed flaw, for example, exposed a way to see otherwise encrypted data after the web server decrypted it. By and large though, HTTPS means the contents of the request (and response) are gibberish to anyone trying to eavesdrop.
Here's the rub: sometimes the contents aren't the only thing you want to keep quiet about. Sometimes you want to hide your identity and location from the web site, or want to hide your destination from lookers-on. HTTPS hides the contents, but not the envelope. Tor - aka onion routing - provides a way to obscure the envelope as well. Tor works by routing your request through several "relays" - individuals or businesses that run the Tor software and voluntarily participate in onion routing. By taking random, ever-changing routes, in such a way that no individual relay knows both the source and the destination, it becomes nearly impossible for an eavesdropper to follow. It also ensures that the destination web site cannot determine the location of the requester - the web site only knows the last relay to pass along the request.
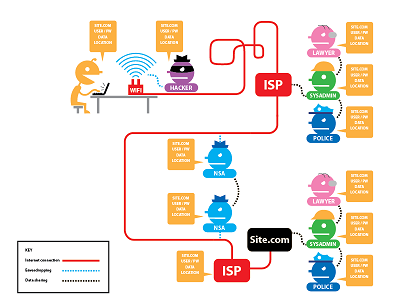 EFF (the Electronic Frontier Foundation - a non-profit organization that supports consumer digital rights and privacy) has a great diagram that clearly shows what HTTPS hides, and what TOR hides (separately, as well as together). HTTPS is great for hiding the contents but not the location; Tor is great for hiding location and identity, but not necessarily the contents. Together, they provide pretty solid privacy and protection.
EFF (the Electronic Frontier Foundation - a non-profit organization that supports consumer digital rights and privacy) has a great diagram that clearly shows what HTTPS hides, and what TOR hides (separately, as well as together). HTTPS is great for hiding the contents but not the location; Tor is great for hiding location and identity, but not necessarily the contents. Together, they provide pretty solid privacy and protection.The single greatest risk in the Tor paradigm is accidentally mixing up activities – doing something in Tor that can be associated with a non-Tor connection. Such as making a purchase using your real address for shipping. Such as reading email that you also read outside of Tor.
Such as logging into Facebook.
Anonymously sharing personally-identifying information is a bit of an oxymoron. Except when it isn’t. What if my real name were not actually David Longenecker, and the photos I share are not really of me and my family and friends? What if this were a pseudonym I use for researching and publishing security flaws, or for communicating with other researchers? In my case, the research I do does not generally put me at risk for criminal backlash. That is not true for others in my field, or in some other fields. I know of some that have faced SWATting, contraband drug deliveries with anonymous “tips” to local law enforcement, and threats against their safety. I know of some whose online persona are intentionally and completely separate from their real identities. They have spent years building a pseudonym, gaining credibility. In those cases, one might want to associate with peers through social media, willingly sharing that online identity, while at the same time keeping their real identity and real location disguised.
And therein lies the benefit of a Tor-enabled Facebook.


