If you manage a high-value Twitter account, consider creating a second, "burner" account. After enabling multifactor authentication on the high-value account, add the same phone number to the burner account. This will turn off SMS access features for the high-value account, without breaking MFA on the same.Updated December 31: Added a description of the variations between mobile app, mobile web UI, and desktop web UI, along with a bug Kevin Beaumont pointed out (described at the end of this post).
On Christmas Eve, Richard De Vere of The AntiSocial Engineer published a doozie of an article describing a serious flaw in Twitter’s security. In a nutshell, if a Twitter account has a phone number connected to it, Twitter accepts instructions via SMS from that phone number, with no additional authentication required.
It gets worse – far worse. Twitter requires a phone number be connected to an account in order to enable multifactor authentication. Twitter does support using a mobile security app or a physical key for MFA, and allows you to turn off SMS-based 2FA, but requires a phone number to be connected to the account nonetheless. Removing the phone number also turns off "logon verification" (Twitter's term for multifactor authentication).

Meaning, a user security-aware enough to set up two-factor authentication to protect their Twitter account, is also opening a back door into their account, a back door that allows functions including follow, unfollow, tweet, retweet, like, DM, turn on or off push notifications, or remove the phone number from the account.
And since Twitter 2FA requires a phone number, sending a “stop” message to Twitter from (or spoofing) the number associated with an account, will disable 2FA on that account, with no notice to the rightful account owner.
That's right: enabling 2FA on Twitter, explicitly enables an SMS back door to Twitter, which can be used to disable 2FA on Twitter, without you knowing that 2FA has been disabled.
Some background
SMS functionality in Twitter began with text notifications - much like one can enable an email notification for DMs and such, one can enable SMS notification for tweets from specified individuals, direct messages, new follows, mentions and replies, retweets, likes, and more.
As De Vere pointed out though, SMS functionality is not limited to notifications. By sending instructions to the SMS short code 40404 (for US users; short codes vary by country, and a long-form phone number works in some locations that do not support short codes), Twitter will take action on behalf of the Twitter alias associated with the sender's phone number.
Oddly, the link on the Twitter settings page to learn more about SMS functionality, is broken, but Twitter's help site has a page documenting SMS-enabled functions. These functions include
- Turn on or off SMS notifications
- Follow [username]
- Unfollow [username]
- Reply to another person
- Retweet another person's most recent tweet
- Like another person's most recent tweet
- DM another person
- Block or Report [username]
- Delete a phone number from the associated Twitter account - thereby disabling 2FA on that account
Two band-aid solutions
The simplest and most complete solution would be for Twitter to offer a setting to enable or disable SMS features for an account. Alas, Twitter has done no such thing. Two alternative solutions come to mind.The first is to set up a "burner" phone number, that is used nowhere else, and not shared with anyone else, and use this number to enable Twitter 2FA. Google voice is one way to do this at no cost. While Google voice is free only for US and Canada phone numbers, there is no requirement that I know of that the phone number connected to a Twitter account be in the same geography as the account holder. One can set up a Google voice number in the US or Canada, regardless of their true location, and access it through the Google voice website or mobile apps.
If you go this route, be sure to not check "Let others find me by my phone number." The whole purpose of this number is to be unknown to potential adversaries.

A second workaround is to connect the phone number to a second Twitter alias - a burner alias. Twitter by design enables SMS features only for the account most recently linked to a phone number. Linking a phone number to a second account still leaves the number connected to the first account, with login verification in effect for the original account, but disables SMS features for that original account.
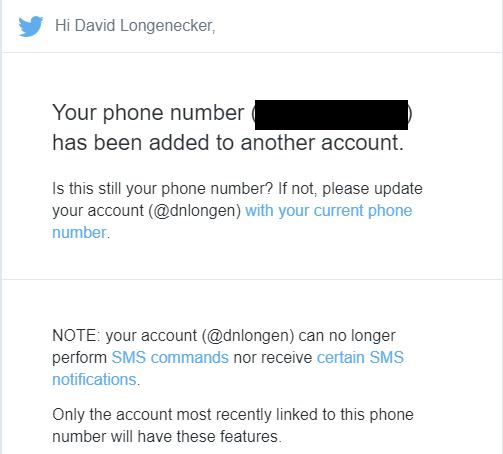
As an added benefit, even if the phone number is subsequently removed from the burner account, SMS features are not re-enabled on the first account.

My preferred workaround? Both: a burner phone number not used anywhere else, used to enable 2FA on my primary Twitter account (which I then change to use a non-SMS second factor), then connected to a second burner Twitter alias.
More quirks and bugs
Kevin "GossiTheDog" Beaumont pointed out a bug in the mobile website UI, where if you delete a phone number, the mobile web settings panel shows login verification (aka multifactor authentication) is still enabled, when in reality Twitter has turned it off and will authenticate using only a password.Note the differences in user experience between the desktop UI, the mobile app UI, and the mobile web UI:
 |
| Desktop UI (Chrome 71.0.3578.98 on Windows 10 Home build 1803) |
 |
| Mobile app UI (version 7.38.1 for iOS 12.1.1, on iPhone) |
 |
| Mobile web UI (Chrome 71.0.3578.89 on iOS 12.1.1 on iPhone) |
Curiously, the mobile web UI only warns that you will no longer be able to receive notifications or login code - it does not say you will disable login verification entirely. In fact, removing the phone number, regardless of whether it is removed through the mobile app, mobile website, desktop website, or SMS command, disables login verification, setting the account back to password-only authentication. The mobile website settings panel though shows login verification still enabled:

As mentioned earlier, Twitter sends no email notification if the phone number is removed from an account by sending a"stop" SMS message. After deleting the phone number using the web UI or mobile app Twitter emails a confirmation to the email address of record for the Twitter account, letting the user know that the phone number has been removed and login verification turned off.
Do you have something to add? A question you'd like answered? Think I'm out of my mind? Join the conversation below, reach out by email at david (at) securityforrealpeople.com, or hit me up on Twitter at @dnlongen
